In today's fast-paced digital landscape, software development teams face the dual challenge of delivering high-quality applications while ensuring robust security measures. This is where DevSecOps comes into play. By seamlessly integrating development, security, and operations, DevSecOps empowers organizations to build and deploy software with enhanced security, efficiency, and reliability. In this blog post, we'll delve into the key components of DevSecOps, explore essential practices, and provide insights into popular tools and techniques.
Continuous Integration and Continuous Deployment (CI/CD)
At the heart of DevSecOps lies the concept of Continuous Integration and Continuous Deployment (CI/CD). CI/CD is a software development practice that emphasizes frequent integration of code changes and automated testing, leading to a continuous stream of deployment-ready software. It enables teams to catch and fix issues early, reduce development cycle times, and rapidly deliver new features to end-users.
With CI/CD, developers commit their code changes to a shared repository, triggering an automated build and testing process. This process encompasses various stages, including code compilation, unit testing, integration testing, and end-to-end testing. By automating these steps, organizations can quickly identify and rectify bugs or vulnerabilities, ensuring a high level of code quality and security.
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST)
In the realm of DevSecOps, two prominent testing methodologies play a vital role in ensuring application security: Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
SAST involves analyzing the source code or compiled code of an application to identify potential security vulnerabilities. This analysis is performed without executing the code, allowing for early detection of issues such as insecure coding practices, input validation flaws, or insecure dependencies. By integrating SAST into the CI/CD pipeline, organizations can catch security issues as part of their regular development workflow, preventing vulnerabilities from making their way into production.
DAST, on the other hand, focuses on testing the application at runtime. It simulates real-world attacks by sending inputs and monitoring the application's responses. This approach helps uncover security weaknesses that may not be apparent from static analysis alone, such as configuration errors, authentication flaws, or injection vulnerabilities. DAST is typically conducted on deployed applications or staging environments, providing insights into potential risks in a real-world context.
Building a DevSecOps Environment
To build a successful DevSecOps environment, organizations must consider several key factors. Here are some essential practices to incorporate:
-
Security as Code
Treat security as an integral part of the development process by adopting the "security as code" approach. This involves using version-controlled security policies, security tests, and security-related configuration files alongside the application's source code. By managing security aspects in code form, organizations can automate security checks and enforce security standards consistently.
-
Collaboration and Shared Responsibility
Establish a culture of collaboration and shared responsibility among development, security, and operations teams. Encourage regular communication, knowledge sharing, and joint decision-making to bridge the gaps between different stakeholders. This collaboration fosters a holistic approach to security, ensuring that security considerations are addressed at every stage of the software development lifecycle.
-
Continuous Security Testing
Integrate security testing into the CI/CD pipeline to identify vulnerabilities early on. Incorporate SAST and DAST tools into your automated testing process, ensuring that code is thoroughly examined for security weaknesses. By continuously testing your applications, you can catch potential vulnerabilities in their nascent stages, allowing for timely remediation.
-
Automation and Orchestration
Leverage automation and orchestration tools to streamline development, testing, and deployment processes. Automation reduces the potential for human error and ensures consistent security practices across the software development lifecycle. It also enables faster and more frequent releases while maintaining high levels of security and quality.
-
Continuous Monitoring and Incident Response
Implement continuous monitoring mechanisms to detect and respond to security incidents promptly. This includes real-time monitoring of application logs, network traffic, and system metrics to identify anomalous activities or potential breaches. By proactively monitoring your applications, you can quickly respond to security incidents, minimizing their impact and reducing downtime.
Popular DevSecOps Tools
Several tools are available to support the implementation of DevSecOps practices. Here are a few examples:
- GitLab CI/CD: A comprehensive CI/CD platform that seamlessly integrates code repositories, continuous integration, and deployment pipelines, along with built-in security scanning capabilities.
- Jenkins: An extensible automation server that supports continuous integration and delivery. Jenkins offers a vast ecosystem of plugins, enabling integration with various security testing tools.
- OWASP ZAP: An open-source web application security scanner that helps identify vulnerabilities and security issues in web applications through dynamic analysis.
- SonarQube: A code quality and security analysis tool that integrates with CI/CD pipelines to provide insights into code vulnerabilities, bugs, and code smells.
- Azure DevOps: A cloud-based platform that offers a wide range of services for development, testing, and deployment, including Azure Pipelines for building CI/CD workflows and Azure Security Center for continuous security monitoring.
Azure Pipeline Flow Chart
Below is a simplified flow chart showcasing the stages of an Azure Pipeline, encompassing continuous integration, security testing, and continuous deployment:
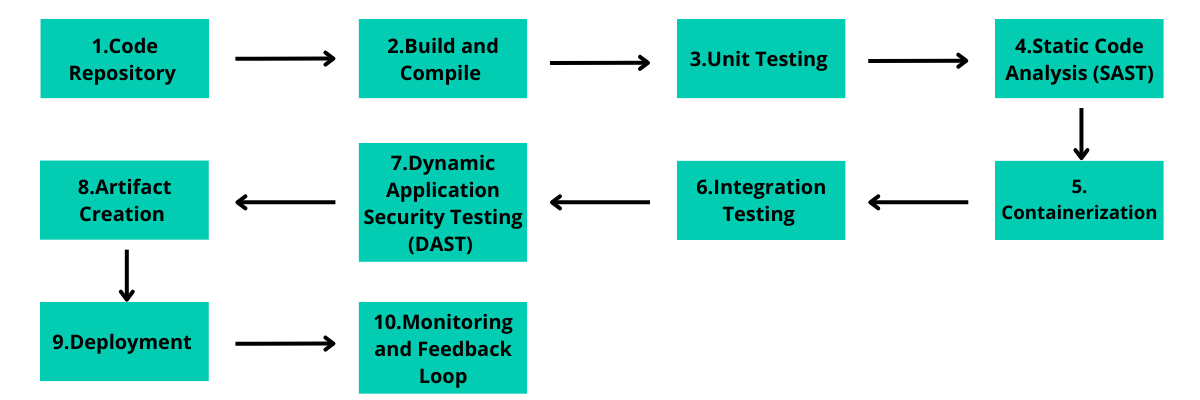
This flow chart illustrates a typical Azure Pipeline flow, where code changes are continuously built, tested, and deployed, while incorporating security testing at multiple stages to ensure a robust and secure software delivery process.
Embrace the Power of DevSecOps
DevSecOps is not just a buzzword; it's a paradigm shift that enables organizations to deliver secure, high-quality software efficiently. By adopting the principles of continuous integration, security testing, and automation, organizations can foster a culture of collaboration, shared responsibility, and innovation. So, embrace DevSecOps, leverage the right tools, and embark on a journey towards secure and efficient software delivery in today's ever-evolving digital landscape








